はじめに
セキュリティを重視するエンジニアリングリーダーは、コード解析ツールを選択する際にSonarQubeとCheckmarxを比較検討することがよくあります。どちらのソリューションもソースコードの問題をスキャンしますが、それぞれ異なるニーズに対応します。SonarQubeはコード品質と保守性から発展し、時間の経過とともに基本的なセキュリティチェックを追加しました。Checkmarxは、脆弱性の発見に特化して構築されたエンタープライズ向けSASTプラットフォームです。急成長するスタートアップから大企業まで、さまざまなチームが開発の早い段階でバグやセキュリティ上の欠陥を検出するためにこれらのツールを検討しています。
各ツールは静的コード分析において重複する部分がありますが、その中核となる焦点は異なります。SonarQubeはコードの健全性を対象とし、バグ、コードの臭い、および単純なセキュリティ問題を検出してコードをクリーンに保ちます。Checkmarxはセキュリティに深く踏み込み、データフロー分析とコンプライアンスルールを通じて複雑な脆弱性を探します。
この比較では、CTO/AppSecリードの視点からSonarQubeとCheckmarxを掘り下げ、両者が異なるチーム規模やセキュリティ目標にどのように適合するかを検証します。
要約
SonarQubeとCheckmarxはどちらもコードセキュリティに取り組みますが、アプローチが異なります。SonarQubeは高速で開発者向けですが、深度が限られています。Checkmarxは徹底的ですが、重く、ノイズが多く、高価です。Aikido Securityは、深いカバレッジとクリーンな開発者エクスペリエンス(誤検知の削減、迅速なセットアップ、すべてを1つのプラットフォームで提供)を組み合わせることで、余計な負担なく本格的なセキュリティを求める現代のチームにとってより良い選択肢となります。
各ツールの概要
SonarQube(基本的なセキュリティを備えたコード品質)
SonarQubeは、コード品質プラットフォームとして最もよく知られています。継続的なコードインスペクションを先駆的に導入し、重複、複雑性、単体テストカバレッジなどのメトリクスを用いてコードの「クリーンさ」を測定しました。長年にわたり、SonarQubeは静的脆弱性ルール、Infrastructure-as-Codeおよびシークレットのスキャン、その他保守性以外の機能を追加することで、セキュリティ分野にも拡大してきました。
しかし、これは専用のセキュリティツールというよりも、「コード品質優先」のソリューションであることに変わりはありません。開発チームはSonarQubeを使用してコーディング標準を強制し、バグや軽微な脆弱性を早期に発見します。多くの場合、品質ゲートのためにCIパイプラインに統合しています。SonarQubeは数十の言語(Java、C#、JavaScript、Pythonなど)をサポートしており、無料のCommunity Editionを提供しているため、多様なコードベースでコードの健全性を向上させるために広く利用されています。
Checkmarx (エンタープライズグレードのSASTプラットフォーム)
Checkmarxは、コードのディープな静的解析を中心としたアプリケーションセキュリティテストスイートです。デプロイ前にSQLインジェクション、XSS、その他のOWASP Top 10の脆弱性を発見するためにソースコードをスキャンします。SonarQubeがコードのクリーンさを重視している点とは異なり、Checkmarxはセキュリティに特化したベンダーによって構築され、テイント解析と広範なルールセットを通じてセキュリティ上の欠陥を発見することに優れています。
このプラットフォームは、幅広い言語とフレームワークのサポート(100以上のテクノロジー)と、コンプライアンスレポートやポリシー管理などのエンタープライズ機能を誇ります。CheckmarxはCI/CDパイプラインや開発者のIDEにも統合でき、コーディング中やマージ前にもスキャンを実行できます。その新しい「Checkmarx One」は、SASTを超えて、ソフトウェア構成分析(オープンソースの依存関係スキャン)、APIセキュリティ、Infrastructure as Codeチェックなどを統合プラットフォームで提供します。要するに、Checkmarxは徹底したセキュリティテストを優先し、より堅牢なツールセットにリソースを割ける組織を対象としています。
機能ごとの比較
セキュリティ機能
SonarQube: 基本的な静的アプリケーションセキュリティテストを提供しますが、深度は限られています。Java、C#、PHPなどの言語で一般的なコードの脆弱性や「セキュリティホットスポット」(手動レビューが必要な領域)を指摘します。Community Editionは、主にこれらの主要言語のセキュリティルールの一部をカバーしています。より高度な検出(例:インジェクションの欠陥に対するテイント解析)には、有料版が必要です。
SonarQubeのセキュリティルールは明白な問題を検出するのに役立ちますが、網羅的ではありません。例えば、ある分析では、SonarQubeが約89の既知のJava脆弱性パターンをチェックするのに対し、CheckmarxはJava向けに300以上をカバーしていると指摘されています。これは、SonarQubeが専用のセキュリティツールであれば検出できる多くの複雑なエクスプロイトを見逃す可能性があることを意味します。これは、単独のAppSecソリューションではなく、一部のセキュリティを伴うコード衛生を改善するための補完として考えるのが最適です。
Checkmarx: 高度なSAST機能をすぐに利用できます。コード内のデータフローと汚染された入力を分析し、ユーザー提供データがエクスプロイトにつながる可能性のある箇所を検出します。Checkmarxは、インジェクション、設定ミス、暗号化の問題などをカバーする膨大な脆弱性ルールセットをサポートしており、多くの場合、OWASP Top 10やCWEカテゴリなどの標準に結果をマッピングします。そのスキャンエンジンはセキュリティのために特別に構築されており、SonarQubeのルールよりもはるかに広範な脆弱性カバレッジを提供します。実際には、チームはコードを整理するだけでなく、ビジネスと顧客を保護するためにCheckmarxを使用して重要なセキュリティホールが検出されるようにします。
さらに、Checkmarx Oneプラットフォームは、SASTとSCA(脆弱なライブラリを検出するため)、DAST(動的テスト)、APIセキュリティ、およびIaCスキャンを組み合わせて、より包括的なセキュリティ体制を実現します。これにより、Checkmarxはコード向けのワンストップセキュリティスイートとなりますが、非常に大規模なものです。
統合とCI/CDワークフロー
SonarQube: 開発ワークフローにシームレスに統合されるように設計されています。CI/CDシステム(Jenkins、Azure DevOps、GitLab CIなど)と連携し、ビルドやプルリクエストごとにコードが自動的にスキャンされます。多くのチームはSonarQubeを品質ゲートとして設定しています。新しいコードが特定の基準(新しい重大なバグや脆弱性がない、十分なテストカバレッジなど)を満たさない場合、パイプラインは失敗します。これにより、品質の低いコードがマージされるのを防ぎます。SonarQubeは、SonarLint(IDEプラグイン)のような開発者向けの統合も提供しており、コーディング中に即座にフィードバックを得られます。
その結果、開発者は普段使用しているツールで問題を確認し、コードがマージされる前に修正できるスムーズなワークフローが実現します。SonarQubeのセットアップには、サーバー(オンプレミスまたはSonarCloud SaaSを使用)とCIパイプラインでのスキャナーの実行が必要ですが、一度設定すれば、開発者にとって最小限の摩擦で「ただ動作する」傾向があります。
Checkmarx: CI/CDおよびIDE統合もサポートしていますが、よりエンタープライズ向けの特徴があります。チームはCheckmarxスキャンをビルドパイプラインに統合し、ゲート処理(例:高深刻度の検出結果があるリリースをブロックする)を自動化することもできます。Checkmarxは、VS CodeやIntelliJなどの人気IDE向けプラグインを提供しており、開発者はエディタ内でコードのスキャンを実行し、結果を確認できます。ただし、実際のワークフローへの影響は異なる場合があります。Checkmarxのスキャンは、多くの場合、より遅く、リソースを多く消費するため、高速なCIパイプラインではチューニングなしにすべてのコミットで実行できない可能性があります。
多くの組織では、開発者の遅延を避けるため、Checkmarxのスキャンを夜間または別のセキュリティパイプラインでスケジュールしています。統合は強力ですが、SonarQubeよりも「軽量ではない」と感じる人もいます。CIの速度に合わせたスキャン閾値と自動化を設定するには、労力が必要となる場合があります。要するに、Checkmarxは開発ワークフローに広く統合できますが、シームレスな体験を実現するには、より注意深い対応(スキャン時間と結果の量を管理するため)が必要となる場合があります。
精度とノイズ
SonarQube: クリーンなコードを優先しますが、実際にはこれがノイズを発生させる可能性があります。開発者はSonarQubeが問題を検出する点を評価することが多いですが、一部からは些細なことが多すぎるとの不満も聞かれます。例えば、SonarQubeは、セキュリティや安定性を真に脅かすことのないコードスタイルの違反や重要度の低い「コードの匂い」を指摘します。G2のレビューでは、あるユーザーがSonarLint(SonarQubeのIDEプラグイン)が時々「無視できる問題を指摘する」ことがあり、不明瞭な場合があると指摘しています。セキュリティに注力するチームは、これらの検出結果を誤検知または単なるノイズと見なすかもしれません。SonarQubeのチューニングは可能ですが(例:ルールの無効化)、初期設定のままでは調整するまで「常にコードが間違っている」と指摘し続ける可能性があります。
セキュリティ面では、SonarQubeのよりシンプルなルールは、Checkmarxよりも実際に少ないセキュリティアラートを生成することを意味します。これは良い点(ノイズが少ない)でもありますが、SonarQubeだけに頼ると、あるRedditユーザーが述べたように「多くの誤検知があり、実際のバグのほとんどが見逃される」というように、実際の問題を見逃す可能性もあります。要約すると、SonarQubeの分析は広範(スタイル、バグなど)であり、開発者を低優先度の警告で圧倒する可能性がありますが、その限られたセキュリティへの焦点は、真に重要なアラートを最小限に抑えます。ノイズからシグナルを区別するにはキャリブレーションが必要です。
Checkmarx: 理論上は高い精度で知られていますが、実際にはトリアージが必要な結果をチームに大量に提示する可能性があります。その高度な分析はより多くの脆弱性を発見しますが、それに伴い誤検知も増加する可能性があります。あるG2のレビュー担当者は、「各プロジェクトに合わせて慎重に調整しない限り、Checkmarxは「多数の誤検知」を生成する」と指摘しています。微調整を行わないと、開発者は実際の問題ではない課題をふるいにかけるのに時間を無駄にする可能性があります。ある不満を抱いたRedditユーザーはさらに、「Checkmarxを使用すると、有効な発見の1%が...99%のゴミ情報に埋もれてしまう」と述べています。これは、既製のルールセットが、特に大規模で複雑なコードベースにおいて、問題を過剰に報告する可能性があることを示しています。
セキュリティエンジニアがルールのカスタマイズ、既知の誤検知の抑制、増分スキャンなどの機能に時間を投資すれば、Checkmarxの精度は大幅に向上します。しかし、それ自体がメンテナンスのオーバーヘッドとなります。良い点は、実際の陽性結果は通常、詳細に説明されることです。Checkmarxは各検出結果に対して詳細なトレースとコンテキストを提供し、曖昧さを減らします。要するに、Checkmarxはより多くのノイズを伴うものの、広範な網を張ります(SonarQubeが見落とす可能性のあるものを検出します)。強力ですが、チューニングなしでは「ノイズが多い」のに対し、SonarQubeは静かですが、網羅性も劣ります。
カバレッジと対応言語
SonarQube: 幅広いプログラミング言語をサポートし、それぞれの言語にルールがあります。人気のある言語(Java、C#、JavaScript、Python、TypeScript、C/C++、PHP、Ruby、Kotlinなど多数)をカバーしており、多言語を扱うチームにとって有用です。SonarQubeの核となる強みは、これらの言語におけるコード品質メトリクスと保守性チェックにあります。セキュリティカバレッジは存在するものの、より狭く、ビジネスアプリケーションにとって最も重要な言語(Java、C#など)に焦点を当てていることが多いです。
特筆すべきは、一部の高度なセキュリティルールは特定の言語の有料エディションでのみ利用可能であることです。例えば、Community EditionにはPythonなどのインジェクション欠陥検出機能がありませんが、Developer Editionには追加されています。また、SonarQubeはサードパーティの依存関係の脆弱性(SCA)やランタイム環境をカバーしません。オープンソースライブラリのリスク管理やインフラストラクチャコードのスキャンがスタックに含まれる場合、SonarQubeだけではそれらをカバーできません。本質的に、SonarQubeのカバレッジはコード品質には優れており、コア言語のセキュリティスキャンには十分ですが、アプリケーションスタック全体(依存関係、クラウド設定など)のカバレッジにはギャップを残します。
Checkmarx: セキュリティスキャンにおいて、業界で最も広範なカバレッジの1つを提供します。エンタープライズの主要言語からニッチな言語、レガシー言語まで、100以上のプログラミング言語とフレームワークをサポートしていると主張しています。この幅広い言語サポートは、多様な技術スタックを持つ大規模組織にとって不可欠です。サポートされている各言語について、Checkmarxは広範な脆弱性クエリルールを維持しており、SonarQubeのルールセットよりも数多く、最新であることがよくあります。言語を超えて、Checkmarx Oneはオープンソースコンポーネントのリスク(脆弱なライブラリに対するSCAチェック)、APIセキュリティテスト、そしてTerraform/KubernetesにおけるIaC設定の問題まで、すべてを統合してカバーします。
これは、アプリケーションセキュリティに対する真のエンドツーエンドのカバレッジアプローチです。トレードオフは複雑さです。これほど広範囲をカバーするということは、より大きな設定負担と結果の重複の可能性を意味します。それでも、C++コードからCloudFormationスクリプトまですべてをスキャンする必要があるセキュリティプログラムにとって、Checkmarxはその広範なカバレッジを提供します。SonarQubeは同様のカバレッジを達成するために他のツールとの組み合わせが必要となります(例えば、依存関係のためにSnykのようなSCAツールを追加するなど)が、Checkmarxは1つのパッケージで包括的であることを目指しています。
開発者エクスペリエンス
SonarQube: 一般的に、より開発者フレンドリーであると見なされています。そのインターフェースと出力は明確さに焦点を当てており、問題はカテゴリ(バグ、脆弱性、コードの臭い)に分類され、重要度によってスコア付けされるため、開発者は簡単に操作できます。SonarQubeのダッシュボードはトレンドとQuality Gateのステータスを提供しますが、開発者はプルリクエストのコメントやIDEの警告を通じて操作することが多く、通常のワークフローを維持できます。Sonarの初期設定は、DevOpsエンジニアが比較的迅速に行うことができます(特にSonarCloud SaaSを使用する場合)。
一部のユーザーからは、SonarQubeのUIが最初は少し分かりにくいこと、そしてオンプレミスインストールにはサーバーのホスティングが必要であるという不満が聞かれます。しかし、多くのレビューでは、一度設定すればSonarQubeが「使いやすい」という点が強調されています。増分解析では高速に動作し、ルールは大きな手間をかけずにチームのニーズに合わせてカスタマイズできます。要約すると、SonarQubeは開発者のツールに統合され、実用的で理解しやすいフィードバックを提供することで、継続的にコード品質を向上させ、開発者を最優先にしています。
Checkmarx: セキュリティの厳格さのために構築されており、そのため開発者体験が二の次になる場合があります。このツールのUIは強力ですが、一部のユーザーからは時代遅れで複雑であると評されています。Checkmarxでの作業は、多くの場合、そのウェブダッシュボードを使用して発見された問題をトリアージすることを含み、コードを修正したいだけの開発者にとってはコンテキストスイッチのように感じられることがあります。スキャン時間も開発体験に影響を与える可能性があります。「クイックスキャン」でもSonarQubeよりも大幅に時間がかかる場合があり、CIで安易に使用するとフィードバックループが遅くなる可能性があります。
良い点としては、Checkmarxは開発者向けの統合を改善しています。結果はJIRAチケットとしてプッシュされたり、VS Codeに表示されたりすることができ、セキュリティの検出結果には開発者を教育するための詳細な説明が含まれています。しかし、一般的な意見として、Checkmarxは導入がより重いとされています。その理由の1つはキャリブレーションの必要性です。開発者は大量の問題にフラストレーションを感じる可能性があり、ノイズをフィルタリングするためにセキュリティチームのガイダンスが必要となります。さらに、Checkmarxをオンプレミスでインストールすることは簡単なプロジェクトではありません(彼らのクラウドサービスを使用しない限り、データベースやオーケストレーターなどが関与します)。テクニカルリードは、その管理のために専任のリソースを割り当てる必要があるかもしれません。
要するに、開発者はCheckmarxを使用できますが、使いやすさの観点からはSonarQubeほど直感的でオーバーヘッドが低いわけではありません。これは開発者だけでなく、セキュリティ専門家のためにも構築されています。
価格とメンテナンス
SonarQube: 階層型モデルを提供しています。Community Editionは無料でオープンソースであり、小規模チームや公開プロジェクトに最適です。有料版(Developer、Enterprise、Data Center)では、より多くの言語、セキュリティルール、エンタープライズ機能が追加されます。SonarQubeの商用版の価格は、通常、解析されるコード行数またはインスタンスサイズによって変動し、非常に大規模なコードベースでは高価になる可能性があります。しかし、多くの中規模チームは、Developer Editionがその価値に対して手頃な価格である(そしてエンタープライズAppSecツールよりもはるかに安価である)と感じています。メンテナンスの観点から見ると、SonarQubeの実行にはサーバー(基盤となるデータベースを持つJavaアプリケーション)のホスティングが必要です。これは控えめな労力で済みます。アップデートは定期的にリリースされますが、アップグレードは簡単です。
一部の組織では、SonarQubeをスケールアップする際にセットアップとメンテナンスが課題となることがあります(データベースの管理、パフォーマンスチューニングなど)。さらに、高可用性などの特定の高度な機能にはData Center Editionが必要であり(非常に高価です)。全体として、SonarQubeは、特に無料ティアを活用したり、必要な機能に限定したりすれば、費用対効果の高いソリューションとなり得ます。そのメンテナンスは経験豊富なDevOpsチームにとっては管理可能ですが、(純粋なクラウドソリューションとは異なり)全く手間がかからないわけではありません。また、SonarCloud(SaaS版)はサブスクリプションで利用でき、メンテナンスを完全にオフロードするため、クラウドサービスを利用できるチームにとってはよりシンプルかもしれません。
Checkmarx: エンタープライズ予算向けに設計されています。プロプライエタリで商用のみであり、無料ティアやコミュニティ版はありません。見込み顧客は通常、価格を知るために営業プロセスを経る必要があり、その価格はしばしば高額であると指摘されています。あるユーザーは率直に、「Checkmarxは比較的高価であり、まず試せる無料版がない」と述べています。ライセンスは、コード行数、プロジェクト数、またはユーザー数によって異なり、完全なデプロイメントの場合、年間数万ドル(またはそれ以上)の費用がかかることがあります。
このため、Checkmarxは多くの中小企業にとって手の届かないものとなっています。メンテナンスも重要です。セルフホスト型の場合、Checkmarxのインフラストラクチャは重厚です(複数のコンポーネント、データベース、スキャンエンジンなど)。専用のハードウェアまたはクラウドのリソースと定期的なアップデートが必要です。ある分析が指摘しているように、セットアップには「時間がかかり、営業担当者と話さずに試す簡単な方法はない」とされています。
Checkmarxは、デプロイメントの負担を軽減するためにクラウドホスト型オプション(Checkmarx One SaaS)を提供することで対応していますが、これにより価格モデルが大きく変わるわけではありません。要するに、Checkmarxは多大な投資であり、堅牢な機能とエンタープライズサポートに対して費用を支払うことになります。CTOは、ライセンス費用とツールを管理するための人員の間で、より高い総所有コストを覚悟する必要があります。これは、組織がCheckmarxが提供する高度なセキュリティカバレッジを真に必要とする場合にのみ価値があります。
Aikidoは、よりシンプルで透明性の高い料金モデル(定額で予測可能)を提供し、CheckmarxやSonarQubeと比較して、規模が大きくなるにつれてはるかに手頃な価格で利用できます。
各ツールの長所と短所
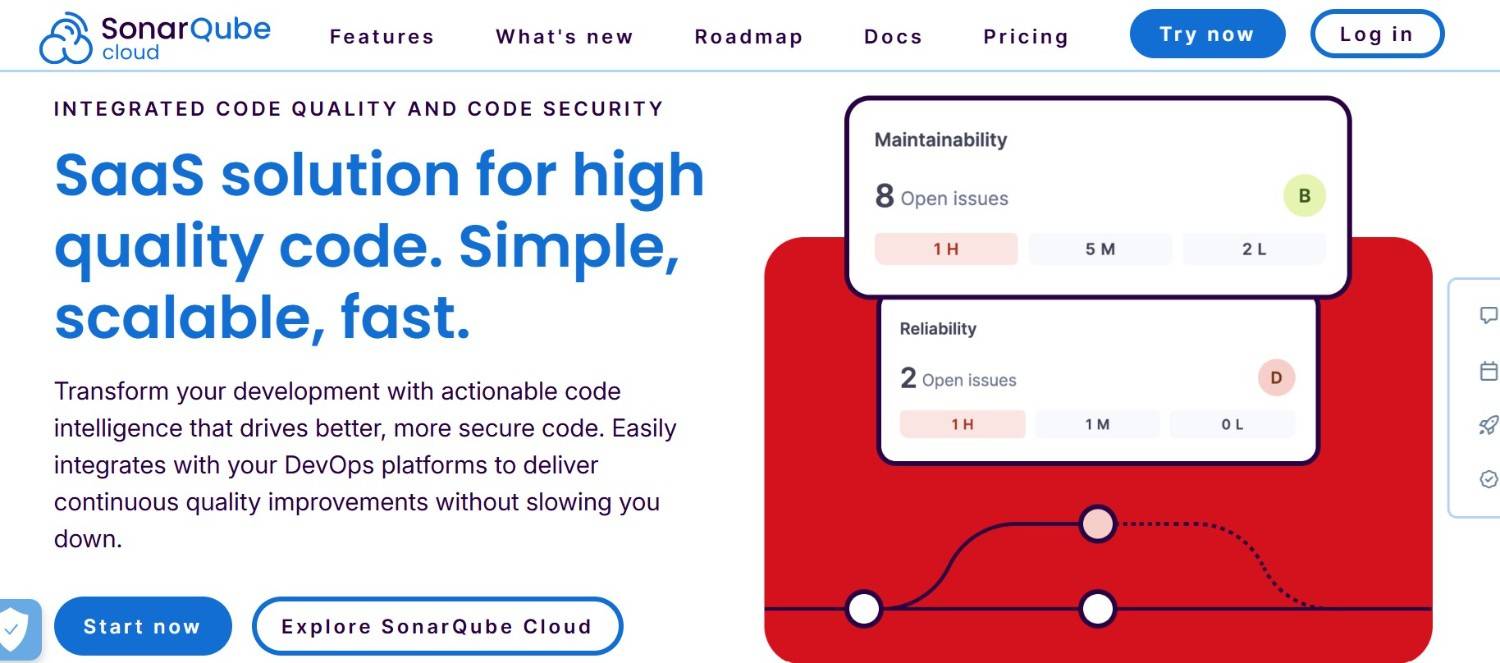
SonarQube – 利点
- 優れたコード品質の強制: SonarQubeは保守性の向上において際立っています。これは、多数の品質メトリクスを通じてコードのクリーンさをチェックする最初の専用ソリューションでした。チームは、コードの臭い、重複、バグを早期に特定し、よりクリーンで信頼性の高いコードにつながる点を高く評価しています。
- 開発者にとって簡単な統合: 開発者はSonarQubeが使いやすいと感じています。CI/CDパイプラインに組み込まれ、プルリクエストやIDE(SonarLint経由)でほとんど摩擦なく即座にフィードバックを提供します。このシームレスな統合により、SonarQubeの導入が開発者のワークフローを妨げることはほとんどなく、バックグラウンドで「ただ機能する」という状態です。
- 幅広い言語サポート: SonarQubeは、主流言語からニッチな言語まで、数十種類の言語をすぐにサポートしています。複数の製品チームを統括するCTOは、フロントエンド、バックエンド、モバイルなど、すべてを単一のツールでカバーするためにSonarQubeを標準化できます。このコード品質に対する幅広いカバレッジは、多様なコードベースにとって大きな利点となります。
- 無償のコアエディション: Community Editionは無償かつオープンソースであり、チームは費用をかけずに開始できます。有償版でさえ、エンタープライズ向けセキュリティツールよりも安価な場合が多いです。このため、SonarQubeは中小企業や品質を重視する企業にとって魅力的です。多額の初期投資なしに、すぐに価値を得ることができます。
- 視覚的なダッシュボードとQuality Gate: SonarQubeのUIは、コードの健全性に関する明確なダッシュボードを提供します。深刻度別に問題を一覧表示し、全体的な品質スコアを提供し、経時的な傾向を示します。マネージャーは、コードが「グリーン」(例:重大な問題なし、カバレッジの改善)であるための基準を設定するQuality Gate機能を高く評価しています。これは、継続的な改善を強制し、進捗を追跡する簡単な方法です。
SonarQube – 欠点
- 限定的な詳細セキュリティカバレッジ: SonarQubeは包括的なセキュリティソリューションではありません。いくつかの脆弱性は検出しますが、そのルールセットとアプローチは真のSASTツールと比較すると浅いです。例えば、Checkmarxなどが検出するような複雑なインジェクションパスを見逃す可能性があります。SonarQubeだけに頼ると、重大なセキュリティの盲点が生じる可能性があります。
- 誤検知とノイズ: 開発者は、SonarQubeが些細な問題を多く指摘しすぎると不満を述べることがあります。特に初期段階では「ノイズが多い」と感じられることがあります。あるユーザーは、ルールを調整するまで“常にコードが間違っていると指摘された”と述べています。一部の検出結果(例:スタイリング、軽微な最適化)は注意を払う価値がないかもしれませんが、それでも表示されるため、チームはアラート疲れを避けるためにルールプロファイルを管理する必要があります。
- 大規模プロジェクトでのパフォーマンス: SonarQubeで大規模なコードベースをスキャンすると、Enterprise機能がない場合、処理が遅くなることがあります。あるレビュー担当者は、スキャンに時間がかかり、Enterprise Editionを購入しない限り並列分析がサポートされないと述べています。これは、大規模なモノレポではSonarQubeがCIのボトルネックになる可能性があり、スキャンを分割する必要があることを意味します。上位エディションではこれを軽減できますが、その分コストがかかります。
- メンテナンスとセットアップのオーバーヘッド: SonarQubeをセルフホストで運用する場合、サーバーとデータベースのメンテナンスが必要です。設定はそれほど難しくありませんが、管理すべきシステムがもう一つ増えます。一部の組織では、セットアップが“複雑”であり、アップグレードや認証システム(LDAPなど)との統合には管理者作業が必要であると感じています。一部のクラウドサービスのようにプラグアンドプレイではありません。
- AppSec機能の不足: 静的コード解析以外では、SonarQubeはオープンソースの依存関係、コンテナイメージ、または動的テストをカバーしていません。最新のAppSecプログラムでは、これらの機能が必要となることがよくあります。そのため、セキュリティのためにSonarQubeを使用しているチームは、完全なカバレッジを達成するために、追加ツール(SCA、DASTなど)に投資する必要があり、ツールチェーンの複雑さが増大します。

Checkmarx – メリット
- 堅牢な脆弱性検出: Checkmarxは脆弱性の発見で定評があります。そのSASTエンジンは高度な分析を使用し、よりシンプルなスキャナーでは見逃されがちなインジェクションや不適切なアクセス制御などの問題を検出します。利用可能な最も広範なルールライブラリ(例えば、Javaだけでも数百の既知のパターン)により、コードがセキュリティ上の欠陥について精査されているという確信を提供します。
- エンタープライズ機能とコンプライアンス: このプラットフォームには、AppSecのリーダーが評価する豊富なレポート機能とガバナンス機能が含まれています。結果はコンプライアンスフレームワーク(OWASP Top 10、PCI DSSなど)にマッピングでき、監査に役立ちます。Checkmarxは、ロールベースのアクセス制御、一元化されたダッシュボード、および大規模なセキュリティポリシーを適用する機能を提供します。厳格なコンプライアンス要件を持つ大企業にとって、これらの機能は大きな利点となります。
- 幅広い技術スタックのカバレッジ: Checkmarxは、ほとんどの競合他社よりも広範な言語とフレームワークをサポートしています。チームがABAP、クラシックASP、または最新のGoやRustでコーディングしている場合でも、Checkmarxはおそらくサポートしています。この広範なサポートにより、すべてのアプリケーションで1つのスキャンソリューションに統合できます。また、IaCテンプレート、APIもカバーし、SCAを統合することで、多くのAppSecニーズに対応するワンストップソリューションとなっています。
- コンテキスト付きの詳細な結果: 開発者とセキュリティアナリストは、Checkmarxの詳細な脆弱性レポートから恩恵を受けます。検出結果にはデータフローの追跡が含まれており、悪意のある入力がどのようにコードをエクスプロイトする可能性があるかを正確に示します。これにより、問題の理解と修正が容易になります。このツールは修正ガイダンスも提供します。SonarQubeのよりシンプルなアラートと比較して、Checkmarxはより多くのコンテキストを提供し、重大な問題の修正サイクルを短縮できます。
- DevSecOpsへの統合: 重量級であるにもかかわらず、CheckmarxはDevOpsプロセスに組み込むことができます。API、CI/CDプラグイン、IDEスキャナーを介した自動化をサポートしています。多くの企業は、セキュリティを左シフトするためにこれを活用しています。例えば、開発者はコミット前にVisual Studioでコードをスキャンしたり、Jenkinsはパイプラインの一部としてCheckmarxを実行し、高リスクの検出結果でビルドを失敗させたりすることができます。適切に設定されると、後期段階のペネトレーションテストを待つことなく、プロアクティブなセキュリティ文化を可能にします。
Checkmarx – デメリット
- チューニングされていない場合の高い誤検知率: 一般的に指摘される欠点はノイズです。Checkmarxの強力な分析は、誤検知でチームを圧倒する可能性があります。あるG2のレビュアーは、「各プロジェクトに合わせて慎重に調整しない限り、誤検知の数が多い」と述べています。大幅なチューニングとカスタマイズがなければ、開発者は問題ではないものを調査するのに時間を浪費する可能性があります。これには、AppSecエンジニアがルールとベースラインを継続的に改善する必要があります。
- スキャンパフォーマンスの遅さ: Checkmarxのスキャンは、特に大規模なコードベースでは遅くなることがあります。ユーザーは、フルスキャンに数時間かかることがあり、開発速度に影響を与えると報告しています。インクリメンタルスキャンや最適化は役立ちますが、標準の状態では、より軽量なツールほど高速ではありません。チームは、スキャンを夜間にスケジュールしたり、CIリソースを増やしたりして対応する必要があることがよくあります。フィードバックループが遅いと、開発者が頻繁にスキャンを実行する意欲を低下させる可能性があります。
- 高額なライセンス費用: コストは大きな障壁です。Checkmarxは、それにふさわしい価格設定のエンタープライズソリューションです。無料ティアはなく、パイロット版でさえ営業担当者との交渉が必要です。あるユーザーは、“最初に試せる無料版がない”こと、そして“比較的高価である”と不満を述べています。予算が限られたチームは正当化が難しく、資金が豊富な組織でさえ、完全なデプロイメントでは珍しくない6桁の価格を考慮すると、ROIを検討する必要があります。
- 複雑なセットアップとインフラストラクチャ: Checkmarxのオンプレミス展開は容易ではありません。複数のコンポーネント(スキャン、結果の保存、ウェブアプリケーションなど)が関与し、インストールと設定には専門家の助けが必要となることがよくあります。前述のとおり、「セットアップには時間がかかります」。そのメンテナンス(パッチ適用、アップグレード、スケーリング)は、ITチームまたはDevSecOpsチームの作業負荷を増大させます。この複雑さにより展開が遅れ、専門的なスキルが必要となる可能性があり、1人のエンジニアが1日でセットアップできるような開発者向けツールとは異なります。
- 開発者ファーストではない: Checkmarxには開発者向け統合がありますが、その全体的なUXはセキュリティプロフェッショナル向けです。インターフェースとワークフローは、迅速な洞察を求める開発者にとっては、ぎこちなく感じたり、圧倒されたりする可能性があります。一部のUI要素は古く、直感的ではありません。強力な社内推進とトレーニングがなければ、開発者は定期的な使用に抵抗する可能性があり、「シフトレフト」の目標を損なうことになります。対照的に、開発者を念頭に置いて構築されたツール(最小限のノイズ、シンプルなUI)は、より高い導入率を達成できます。
Aikido Security: より良い代替策
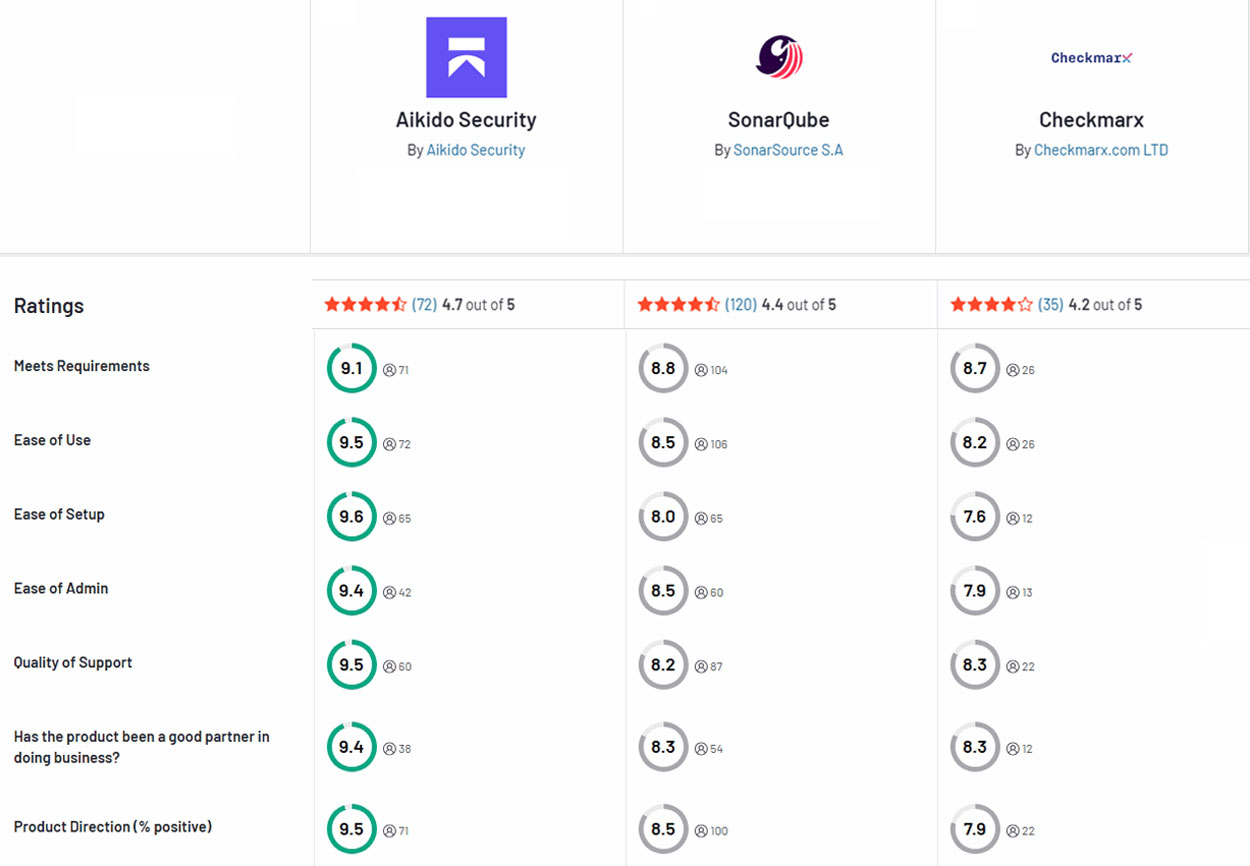
Aikidoは、CheckmarxのカバレッジとSonarQubeのシンプルさを、ノイズやオーバーヘッドなしで兼ね備えています。SAST、SCA、IaC、コンテナ、シークレット、APIスキャンといったフルスタックのセキュリティスキャンを、すべて1つの開発者向けプラットフォームで提供します。Aikidoを際立たせているのは、低い誤検知率と迅速なセットアップです。チームは最小限のトリアージで実用的なアラートを受け取れます。Git、CI/CD、IDEに直接統合され、個別のダッシュボードや大規模な展開は不要です。
また、より安価で透明性が高いです。フラットな価格設定、充実した無料枠、煩雑な営業プロセスなしで、チームは数分で開始できます。浅すぎる(SonarQube)と複雑すぎる(Checkmarx)の間で迷っているなら、Aikidoがバランスを取ります。



